before you design a security system, decide what threatens and how
Risk Assessment is the Vital First Step in Securing the Enterprise
If you want your security systems to be of most benefit, be sure you include the planning step often overlooked: a risk assessment. Why often overlooked? People may already be familiar with common aspects of physical security and become used to certain configurations in their work experience. Because of this, they feel ready to quickly define what they want however, the most important question which should first be answered is this: “What do I really need to protect and from what”?
Starting with this question it is possible to develop a protection scheme which has a high likelihood of success because it builds on knowledge of your operations. A full security risk assessment also yields a basis for calculating return on investment (ROI) in the proposed solutions. This enables management to properly evaluate and buy-in to your recommendations.
Let’s discuss what a physical security risk assessment is and how you may implement one. We will also note how your security integrator can help you with this endeavor.
Common Business Risk Assessments
Risk Assessments occur more often in your enterprise than you may think. What are some common risk assessments?
Business insurance – whether it be property, liability or otherwise – involves risk assessment. How is the cost of your coverage calculated? Actuarial calculations are made of the common risks for your specific business and the cost to insure leverages share resources pooled with other businesses and institutions. Annual updates are typical.
Fire safety and protection systems are also designed based on risk. They follow prescriptive codes such as NFPA 72 which is developed by regular analysis of fire hazards. For larger structures engineering work is done to match the specific fire hazards of the operation with the level of protection required. This fire hazard risk assessment is updated if the building structure or operations change.
Information security assessments are a recent phenomenon and determine the protection required to keep enterprise systems from purposeful attacks, errors and environmental and structural failures. Physical electronics security is almost always part of the protection plan. Because cybersecurity threats are so prevalent and evolving, some actually engage consultants to constantly probe their IT systems in order to reveal vulnerabilities. In other words, the risk can be so great that the threat analysis is near continuous. [Editor’s note: The solutions are so often intertwined with electronic security we include an information security guide in our reference list].
This brings us to general security risk assessments. These assessments are the evaluation of vulnerabilities with the goal of determining what are the appropriate security measures to be taken. The threats almost always involve human actors and the assets to be protected can be people, structure, equipment, processes, continuity of operations, information, reputation, etc. The potential losses and likelihood of security events are calculated and compared with the cost of candidate security solutions. The goal is to define a set of recommendations for enhanced security as well as the returns on such an investment. In this article we will focus on this type of assessment.
Physical Security Risk Assessment
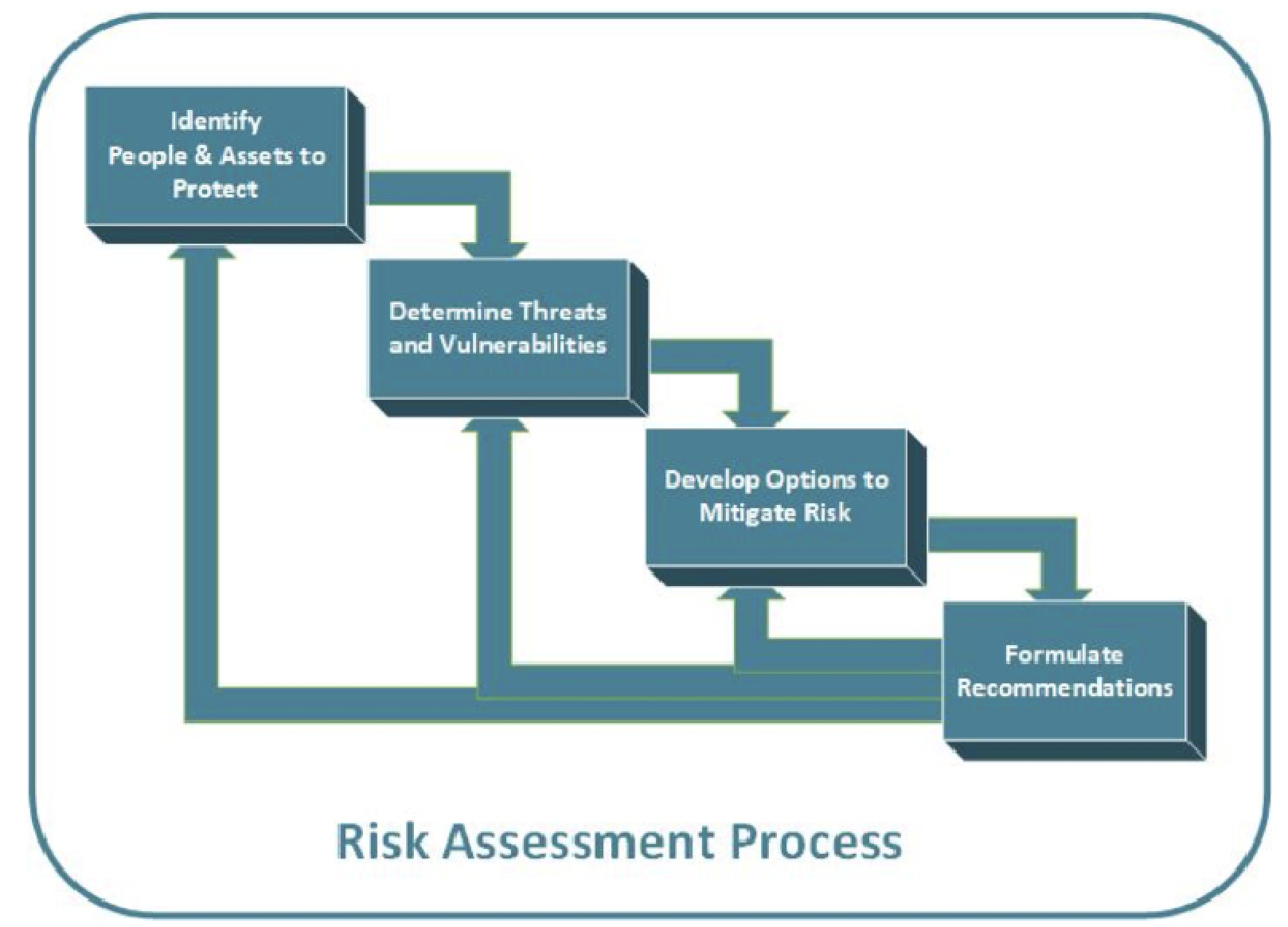
In a physical security risk assessment, there are four main tasks:
– Define the people and assets you need to protect
These assets can include the building and equipment, but also confidential information, operational continuity and stocked goods or material. In many cases reputation and good will is of paramount concern (an example being retail businesses which handle sensitive credit card information).
Of course, people are the unique and greatest asset. We uniquely value our employees or clients which is why we usually say; “People and Assets”. Because of their unique value, protection of people leads to more subjective ROI calculations than impersonal assets.
– Risks and vulnerabilities
What are the security risks to your people and assets? The most common and traditional risks have been burglary, threatening equipment and stock. Also, the possibility of fire threatening building structure, people and operations. In retail loss pilferage by shopper or employee has been the traditional concern for a number of decades.
In more recent times incidents leading to legal liability, disrupting continuity of operations, and loss of business reputation have moved up the list. Vulnerability to lawsuit is often now the number one or two concern of some enterprises. We recently encountered an institution operating a dozen sites with daycare programs supporting several thousand families. Their annual legal budget was over 5 million dollars and the biggest issue were civil lawsuits. For them, the enhanced video surveillance needed to protect both the children and their caregivers did not even have to be run through an ROI calculation.
Another risk that has emerged in the last decade is the active shooter scenario. While the probability is still exceedingly low the consequences are so terrible that every larger operation now needs to consider it.
– Options to mitigate
How will you reduce the threats to a manageable level? In answering this a variety of solutions are usually involved. These include physical design of the site, operational policies and electronic security. This is where the active participation by design-build security integrators can benefit you. An electronic tool which has literally reduced in cost by an order of magnitude compared to useful function in the last decade is video surveillance. As you craft your solutions compare the budgetary cost with the value of protection offered.
– Formulate recommendations
This often requires at least 2 or 3 iterations where the cost of solutions are compared to the return on investment. Budgetary limitations can often lead to a phased approach.
Defining Threats And Their Probability
This is often the most difficult to assess but doing this well in particular is the key to success and will be what management scrutinizes the most. After drafting an initial set of vulnerabilities enlist other operational managers in order to get a current and complete picture. Below is a sample table of threat definition, also a site assessment form for a definition of the current security status:
Perhaps most difficult is defining the probability of each risk event. Stochastic definitions provided by standards can quickly remind you why you may have hated math. The effective shortcut – and this is typical – is to rely on empirical data provided by publicly available statistics. Examples are general crime statistics which you can extrapolate for your locale and operations.
Each industry also usually publishes data of both likelihood and impact of events. In the retail industry RILA annually publishes retail loss statistics which thoroughly map typical employee and customer misbehavior and the cost of each type of event. If you are in this industry you can often adapt this data to your situation.
You may also research any internal data based on your own history. This can include past insurance claims and other losses.
Security Design To Mitigate Threats
There are basic norms in electronic security today. Fire and burglary protection is so standard it is regulated and discounted for by insurance. Basic access control and video surveillance of entrances and exits are also becoming the expected minimum.
Similarly, there are structural security features which have become standard. There is a reason why larger operations all have that distinctive trough in their exterior landscaping or bollards – to hamper vehicular assault on the site. Visitors are typically directed to a single entrance, etc.
The impetus for a risk assessment is to what extent this security is deepened. A good design-build integrator is invaluable as a participant in developing this. He can provide you the latest cost-effective and creative solutions to consider.
To what extent will you use surveillance for your exterior or interior? Will you use access control with your interior spaces or even your vehicle entrances? Will you enhance your information security by adding access control to your IT closets and server room? Will you upgrade to industry standard encryption and authentication of access privileges?
Response time to threat is also a growing consideration. Fire and burglary monitoring is standard but what about duress notifications by panic buttons – wired or wireless? Analysis of active shooter scenarios show that reducing detection and alert time is the key to saving life. Are the newer shot detection technologies a possibility for your operations?
Consider the new drone technology. Already surveillance drones are being used for video escorts and guard tours. This robotic technology will only develop further as a security tool and will rapidly develop as cost-effective. This is a further example of how technology developments can adjust risk assessment recommendations.
What Is Your Return On Investment
Return on investment is the net benefit over a period of time compared to the investment required. This is often expressed as a ratio of the two. The net benefit you are seeking is to – not entirely eliminate but instead – reduce or mitigate your threats and potential losses to a workable level. Today operations like to see the desired results equivalent to the investment within one or two years of the expenditure. This often defines what can be recommended in the assessment.
If however the need for protection overwhelms the budget financing such as capital or operational leases can leverage the money available to reach the protection needed in time. It is also useful to note that while some electronic systems have an anticipated lifetime of five years, security equipment is often in place for one or two decades before major upgrades. And even then, creative integrators can extend the life of some original elements like wire for 30 or 40 years.
There are intangible benefits which are difficult to quantify. We performed work at a university which was famous globally but whose neighborhood had become crime infested. The school invested millions in electronics security. As guides would walk prospective students and their families through the campus a key benefit they would point out was the obvious video surveillance and access control. This illustrated how important the protection was to the schools very value stream.
Another example of subjective intuition beyond calculation was the decision early on by some experienced founders of a housing startup. They focused on rehabilitating historical housing to the benefit of rundown neighborhoods. They also decided to invest in 3 or 4 times more security technology compared to neighbor operations. The first installation helped win a national HUD award as crime at the complex was reduced to a fraction of what it was before. Over the following decade the security of their sites became a signature feature which attracted ever-growing support by politicians and public administrators. This was because of how effectively their security mitigated problems. The extent to which security benefitted exceeded any assessment.
Don’t Hesitate To Perform A General Risk Assessment
Please find in the sidebar below a summary of the essential steps for a general security assessment. A well – executed risk assessment will give you clear direction as to how to best secure your operations and provide a basis for management to authorize your plan. While some aspects can be challenging, those involved always develop greater knowledge of their operations. Most importantly, your workplace will become as secure and stable as is possible. ■